Cybersecurity is a rapidly growing field. Given the emergence of the digital economy, there’s a high demand for the services of cybersecurity professionals.
The Bureau of Labor Statistics’ data shows that IT security jobs pay thrice as much as the average salaries of other full-time positions. However, the high salary comes with a huge amount of responsibility. After all, businesses are entrusting their digital network to these cybersecurity experts.
Just like any other job in the world, you’ll need to ace the interview before you land your dream job as a cybersecurity analyst. Here are 25 of the most commonly asked cybersecurity interview questions and how to answer them!
25 Most Popular Cybersecurity Interview Questions
The demand for a cybersecurity engineer is fast increasing. As a result, there is fierce compeition to land a cybersecurity position. However, to secure such a role, you must be fully equipped to answer cybersecurity interview questions.
Having essential cybersecurity skills is part of the equation. In addition to this, you must also be well-prepared to pass the cybersecurity interview questions.
These are the 25 cybersecurity interview questions and answers to help you get fully prepared.
1. What Is Cryptography?
It is a technical and practical study in IT security used primarily for safeguarding data and preventing unauthorized access.


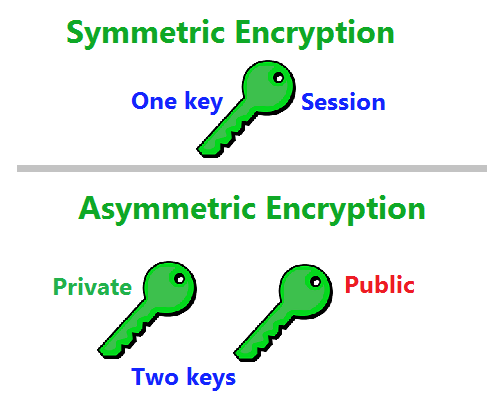
2. Give The Difference Between Symmetric And Asymmetric Encryption
Symmetric encryption utilizes a single key to encrypt and decrypt files. However, asymmetric encryption utilizes varying keys to encrypt and decrypt files. Although symmetric encryption is faster, it transfers over an unencrypted network. Asymmetric encryption offers better security, but the system is slow.
To get the best out of the two worlds, a hybrid approach that makes use of the fast symmetric process and the secure channel of asymmetric encryption is better.

3. What Is The Difference Between IDS And IPS?
IDS means intrusion detection system. It only discovers an intrusion and does nothing to mitigate it. Furthermore, it leaves that aspect to the administrator’s discretion.
IPS means intrusion prevention system. Hence, it detects and prevents intrusion.
The two systems are also positioned differently in a network even though they make use of one fundamental concept.


4. Explain CIA Triad Or CIA Triangle
CIA is a network security term that refers to data Confidentiality, Integrity, and Availability.
Confidentiality ensures that only authorized individuals can have access to data through strong encryption.
Availability ensures that authorized individuals have access to data anytime they need it.
Integrity ensures that the data made available to an authorized individual remains as it is. This means that there should be no alteration from unauthorized personnel.
5. Differentiate Encryption And Hashing
Encryption and Hashing both convert files into unreadable forms. However, an encrypted file can decrypt back to the primary state while a hashed file cannot.
A security engineer can reverse an encrypted file, though he cannot reverse hashing. Besides, encryption maintains confidentiality, while hashing maintains the integrity of files.


6. What Is A Firewall And Its Use In Network Security?
A firewall is a restrictive system used in network security to monitor and regulate network traffics. While it permits authorized entries, it limits unauthorized entrance from cyber threats like viruses, worms, malware, and more. Furthermore, firewalls equally limit distant access and filtering of contents.


7. What’s The Difference Between Software And Penetration Testing?
Software testing is an IT security strategy that concentrates on the features of software rather than on its network. Penetration testing, on the other hand, is an IT security technique used to discover and manage security susceptibilities.
8. What Is Web Server Hardening?
Webserver hardening is the process of sifting through redundant services than run on different ports. Moreover, it is also the elimination of default trial codes from the servers. That’s just the basic explanation of server hardening. Businesses will commonly utilize a custom-made checklist to harden their servers. Besides hardening new servers after creation, a cybersecurity engineer needs to redo the hardening process and the checklists every year.
9. Differentiate HIDS And NIDS
HIDS means host intrusion detection system. NIDS, on the other hand, means network intrusion detection systems. The two network security systems work for intrusion detection. However, HIDS is configured to monitor a specific host or device for suspicious activities. NIDS, on the contrary, monitors an entire network security traffic of all devices in a network for suspicious activities.
10. Define SSL Encryption In Network Security
SSL is a network security term which means Secure Sockets Layer. It is a widely-accepted IT security standard of encryption between a web server and a web browser. This may be one of your interview questions as a security analyst.
It helps to maintain the privacy and security of data in digital a business environment. Secure Sockets Layer is, therefore, encryption and decryption processes used by secure servers to protect data from being intercepted by unauthorized parties.
11. What Is SQL Injection In IT Security, And How Can You Prevent It?
SQL Injection (SQLi) is a script injection attack that occurs when a cyberterrorist influences the data during its transfer to a server to implement malicious SQL scripts. At the same time, it takes control of the web app’s database of the server.
Furthermore, SQL attack breaches network security and leads to unauthorized access, modification, and delete of data. The main aim of this attack is to take control of database servers.
To prevent SQL Injection attacks, a cybersecurity analyst will make use of prepared scripts, stored processes, and ensures to validate user inputs before transferring them to the server.
12. What Is Data Leakage?
Data leakage is both a deliberate or unintended transfer of a company’s data outside the company to an unapproved location or target.
A company’s data can leak out through either accidental or non-accidental breach by staff or through criminal activities of hackers. In IT security, a security engineer tries to prevent data leakage with DLP or Data Leakage Prevention tools. These tools include software and processes.
13. Name The Most Prevalent Types Of Cyber Attacks
As a cybersecurity engineer, you need to know the prevalent cyber threats. Along with this, you should also know what to do to prevent such threats. The most commonly reported types of cyber attacks include the following:
- Malware
- Man-in-the-middle attack
- Phishing
- Password attacks
- DDos
- Man in the Middle
- Drive-By Downloads
- Malvertising
- Rogue software
14. What Is A Brute Force Attack? How Can You Prevent It?
Brute Force attack is a strategy used by cyber attackers. What they do is guess the current credentials of people by trial and error. They can do this by repeatedly combining different versions of an individual’s parameters.
Some brute force attacks use automated processes to login into a target user’s account using a combination of the person’s credentials. To prevent brute force attacks, use complex and lengthier passwords with both text, numbers and characters. A good security engineer will additionally implement login attempt limits.
15. Define Port Scanning
Port Scanning is a network security procedure utilized by security analysts to discover open ports and available service on a host. Cyber attackers utilize port scanning to gain information about a vulnerability they can explore.
Network security analysts make use of port scanning to check the security protocol of a network. A few widely utilized port scanning procedures are Ping Scanning, TCP Half-Open scan, TCP Connect scanning, UDP scan, and Stealth Scanning.
16. Define Multi-factor Authentication (2FA)
Multi-Factor authentication is an additional level of security implemented by security engineers to ensure data security. In this case, a user doesn’t only use a secure password login. He uses the second method of security that only the user has access to like his phone in the case of a text verification, voice call or a physical token.
17. What Is VPN?
A VPN or Virtual Private Network is utilized for creating a safe and encrypted network security system. With a VPN, client data is transferred to a socket where it is encrypted. After that, the data is then transferred through the network to another socket. Usually, the data is decrypted and transferred to the server.
All the response of a server passes through a secure VPN socket for encryption. Likewise, the data travels in an encrypted form to a VPN point that decrypts and transfers the data to the client. The essence of a VPN is to ensure data security and privacy during the process of data transfer.
18. What Do Risk, Vulnerability, And Threat Mean In Network Security?
A threat is an individual who can potentially cause harm to a network system or an entire company. Vulnerability is a system flaw that attackers can exploit to launch their attacks.
On the other hand, a risk is a possible loss or damage that could result if attackers utilize system flaws to launch their fraudulent attacks.
19. Differentiate White Hat Hackers, Grey Hat Hackers, And Black Hat Hackers
White hat hackers are ethical hackers. They use their knowledge to work as security analysts and patch up any security flaws in a company system.
Black hat hackers, on the other hand, utilize their knowledge to hack into security networks. Moreover, they write malware scripts and injects them into a system to steal users’ data. After that, they take over hacked systems and utilize them for malicious purposes.
Grey hat hackers are ethical hackers. They occasionally search for security flaws in software and systems without authorization from the owner. Furthermore, they report any flaws they find to the company.
20. What Is The Required Frequency Of Patch Management Operation?
When launching, you should implement any security patch management at the moment. If using a Windows server, you must implement the patch management operation within thirty days of release. Moreover, he should equally do the same for network devices soon after the patch release.
21. Define Cognitive Cybersecurity
Cognitive Cybersecurity involves the use of AI technology processes to figure out possible cyber threats. Accordingly, it secures and safeguards physical and digital devices and systems.
Self-learning or cognitive security processes make use of data mining, design identification, and natural semantic procedures. Through these, they can mimic the human brain in an influential computer model.
22. What Is MITM Attack, And How Do You Prevent It?
A MITM attack, also known as Man-in-the-Middle, is a cyber attack where the attacker positions himself or herself between the message of two parties. Their objective is to steal some useful information. The hacker impersonates one of the two parties and sends a message to the other party in disguise.
When one party sends the information unknowingly to the hacker, the hacker redirects the data to the party. He uses the message for extracting useful information.
A few ways to prevent the man in the middle attack is through VPN, strong encryption, secure passwords, authentication system based on the public key, and force HTTPS implementation.
23. Give the Meaning Of DDOS Attack. How Do You Prevent It?
A DDOS attack means Distributed Denial of Service attack. It is an attempt by hackers to flood a server with false traffics that jam-packs the system. This prevents a business from offering its services to its credible customers.
Furthermore, this can come in the form of a flooding attack. Through this, the hacker sends a large amount of traffic to the target system, causing the server to malfunction. The second method is a crash attack. It is where the hacker leverage on a server bug to crash a system. Additionally, this attack prevents the business from rendering service to genuine customers.
A few methods used by security analysts to prevent DDOS include the following:
- Anti-DDOS systems
- Firewalls and Router configurations
- Use Front-End Hardware
- Balancing of loads strategy
- Traffic Handle Spikes

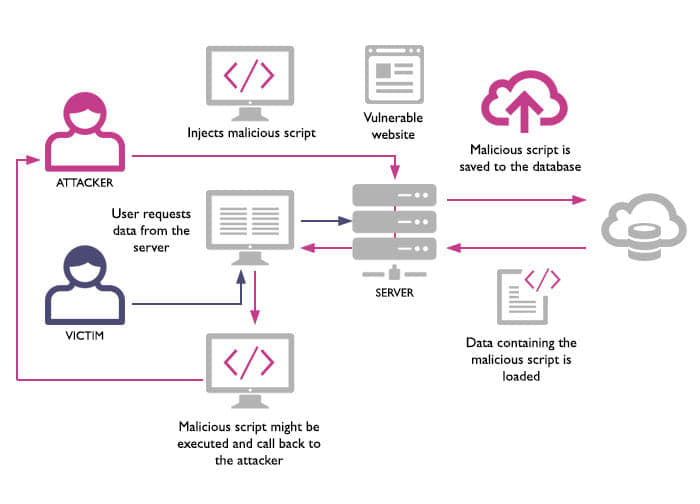
24. What Is XSS Attack And How Can You Prevent It?
XSS or Cross-Site Scripting attack allows hackers to introduce malicious scripts on the client-side into web pages. Moreover, hackers make use of XSS attacks to hijack network sessions. At the same time, they manipulate data which can be in the form of stealing cookies, DOM modification, distant code implementation to crash a server.
The IT security methods used by security engineers include input validation, CSP implementation, user inputs validation, sanitization of user inputs, special character encoding, XSS HTML filtering, and through the use of Anti-XSS network security tools.

25. Discuss In-transit Data Protection And Data Protection At Rest
Data protection in transit is when you protect data that travels from server to user. However, data protection at rest is the protection offered to data when it is stored in the database or a hard drive.
The security of data is reduced when in motion. For this purpose, cybersecurity analysts should be able to devise ways to protect data while in motion. Consequently, data at rest is more secure than data in transit.


Importance Of Cybersecurity In Industry 4.0
Industry 4.0 (the fourth industrial revolution) has a close link with cybersecurity. Moreover, the development of this industry comes with a fresh operational risk for associated producers of smart technologies along with their digital supply networks.
Cyber attacks are more prevalent now than in the past. Furthermore, producers of these emerging technologies as well as their supply chains may be ill-prepared.
The rapid appearance and growth in the amount of Industry 4.0 cybersecurity breaches also stress the need for more cyber flexibility. For adequate maintenance of IT security in the face of industry 4.0, cybersecurity tactics must be securely, cautiously, and resiliently implemented. Likewise, complete incorporation of network security to the organizational and IT processes from inception is needed.


Cybersecurity Threats On Businesses
An example of this is the 2009 Stuxnet malware incident. On that incident, the hackers injected independent networks with flash drives and altered centrifuge speeds in a nuclear plant. The Stuxnet’s cyber-attack is an example of the far-reaching effects of cyberattacks against connected chains of IT manufacturers.
Furthermore, we should equally be aware of the inherent cyber risks posed by enterprises. These enterprises make use of smart and interconnected IT solutions. This is to revolutionize, alter, update, and make strategic business decisions. Moreover, the fresh and evolving risks posed by the connectivity of smart devices need attention.
An example is the case of manufacturing industries. They are starting to make use of the Internet of Things (IoT) and Industry 4.0 products. To address these cybersecurity threats, any industry 4.0 solution must make cybersecurity considerations. These should be the primary part of their business tactics, structure, and processes from the onset.
Final Words
Industry 4.0 boosts digital capacities in the production and supply chain procedures. Moreover, it comes with fresh cyber risks in which the industry is ill-prepared.
The increasing cyber threats from exterior forces and the overreaching potential impacts of a cyberattack lead to the increasing demands for cybersecurity analysts.
As a cyber-security engineer, you need to arm yourself with these networking security interview questions. This way, you can stay on top of the competition. At the same time, bear in mind the responsibility that comes with the role.
























